SHA-512
Technical research assignment analyzing the SHA512 hashing algorithm.
What is SHA-512?
SHA512 is a member of the SHA-2 family developed by NIST in 2001. It is a cryptographic hash function that generates a 512-bit hash value, typically represented as a 128-character hexadecimal number. SHA-512 is designed to be a one-way function, meaning it's practically infeasible to reverse the hash back into the original data or find two different inputs that produce the same hash.
What is Hashing?
Hashing is a method used in cybersecurity to secure data. It transforms input data into a fixed-length string of characters, which appears random. This is widely used in password storage, file integrity checks, and digital signatures because even a slight change in input results in a dramatically different hash.

Figure 1. Example of hashing data using SHA-512.
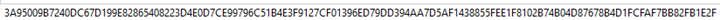
Figure 2. Even the smallest change to input results in a very different hash output.
Examples of Where SHA512 is Used
- Data Integrity Verification
SHA-512 is used to ensure data has not been altered. When downloading files, SHA-512 hashes are often provided so users can verify the integrity of the file by hashing the downloaded file and comparing it to the provided hash.
- Digital Signatures
Digital signatures use SHA-512 to create a hash of the signed content. This hash is then encrypted with a private key to create the signature. When verifying the signature, the recipient hashes the content again and decrypts the signature using the sender's public key. If the two hashes match, the content is verified.
- Password Storage
SHA-512 is sometimes used (ideally with salt) to hash passwords before storing them in a database. This ensures that even if the database is compromised, the actual passwords are not exposed in plaintext.
- Blockchain and Cryptocurrencies
Although more common in SHA-256, SHA-512 is also used in certain blockchain technologies to secure transaction data and maintain the integrity of blocks.
Pros and Cons of SHA512
Pros:
- Strong security – resistant to collision and pre-image attacks.
- Large hash size – good for high-security applications.
- Widely supported – used in major libraries and protocols.
Cons:
- Slower than SHA-256 – more computationally intensive.
- Larger output – not necessary for all applications (overkill in low-risk environments).
- Not suitable for password hashing alone – should be used with salt and key stretching algorithms (e.g., bcrypt, PBKDF2).